Sep 06 2023
- Slashing, a primary risk of staking on Ethereum, is when a percentage of the ETH staked to a validator is programmatically seized from the validator for misbehavior. If more validators are slashed, the penalty per validator becomes worse.
- This penalty factor means that correlated slashing, or the simultaneous slashing of multiple validators due to a shared point of failure or correlated misbehavior, presents an even steeper risk to stakers.
- The Liquid Collective liquid staking protocol aims to mitigate the risk of correlated slashing with a multi-operator approach, programmatically staking ETH round-robin across a diversified set of enterprise-grade Node Operators. The protocol also requires that each independent Node Operator runs multi-cloud, multi-client, multi-region staking infrastructure, implements double-signing protection, and meets security and compliance standards.
- To further mitigate against the risk of slashing, Liquid Collective offers a comprehensive Slashing Coverage Program for all LsETH holders covering both network-wide events and Node Operator failures.
While global participation in staking to secure proof of stake (PoS) networks continues to grow at a rapid pace and liquid staking has taken over the charts as the single largest sector of DeFi, many participants still lack a clear understanding of staking’s core risks and how to mitigate against them.
Slashing, a primary risk of staking on Ethereum, is when a percentage of the ETH staked to a validator is programmatically seized from the validator for misbehavior. If more validators are slashed, the penalty per validator becomes worse.
This means that correlated slashing, or the simultaneous slashing of multiple validators due to a shared point of failure or correlated misbehavior, presents an even steeper risk to stakers—one that can be amplified by staking with single operator staking providers, making it a key consideration for those evaluating options for staking participation.
In this post we’ll cover how correlated slashing works in Ethereum, the risks it presents, how these risks can affect liquid staking protocols, and tactics for mitigating correlated slashing risk.
Correlated slashing: an overview
The Ethereum network relies on validator nodes to propose and attest to blocks. Validators are required to lock-up a certain amount of ETH as collateral to register on the network (currently ≅32 ETH). Slashing is the protocol's way of penalizing validators for malicious behavior or liveness faults.
Correlated slashing can happen in several scenarios, including:
- Shared infrastructure: Validators being operated by the same node operator, or running on the same cloud service or data center, can be slashed simultaneously if the node operator or shared service experiences downtime or is compromised.
- Client software bugs: If multiple validators are using the same client software and that software has a bug, it could lead to correlated slashing.
- Sybil Attacks: An attacker controlling multiple validators could intentionally act maliciously, leading to the slashing of all controlled nodes.
In addition to Ethereum’s base slashing penalty (currently 1/32 of the validator’s effective balance, or ≅1 ETH) and the forced exit of the validator to Ethereum’s exit queue, Ethereum’s slashing calculation also includes a correlation penalty. This is an additional penalty designed to discourage validators from colluding or oversharing the same infrastructure. The more validators that are slashed around the same time, the higher the correlation penalty.
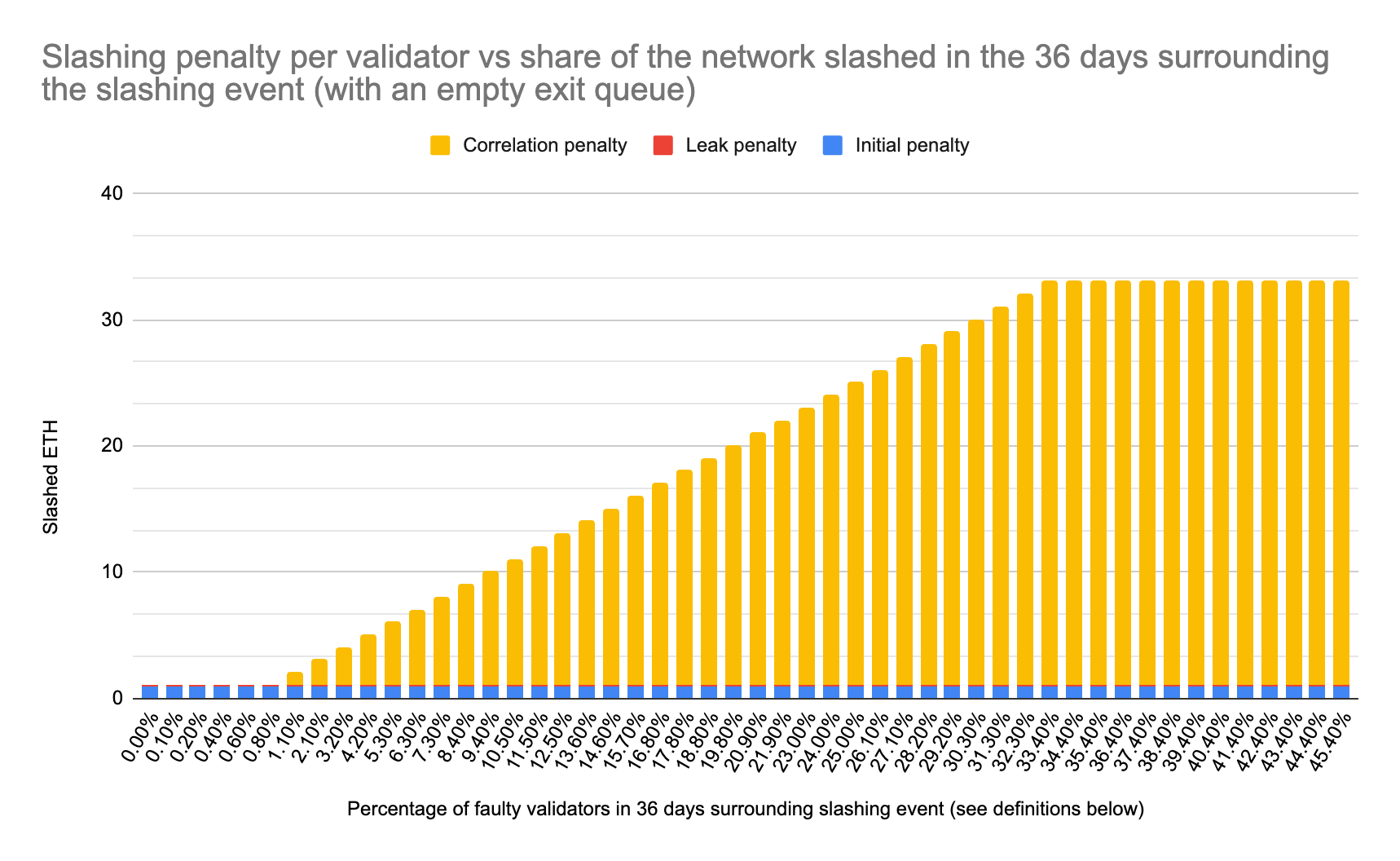
This penalty is calculated based on the proportion of the total validator set that has been slashed within a recent period (currently over the most recent 8192 epochs, or ≅36 days). For example, if about 1% of the total validator set is slashed, the correlation penalty is 1, but if about 3% is slashed, the penalty is 3.
Notably, if 33.4% or more of Ethereum’s validators are slashed the correlation penalty is 32, leading to 100% of the validator’s 32 ETH effective balance being programmatically seized by the network. This is a protection against any one operator putting Ethereum’s security at risk by operating more than 33% of the network’s validators.
As such, staking with an operator who runs more than 33% of the network’s validators puts the staker at a heightened risk of losing up to 100% of their staked funds due to a correlated slashing incident. A correlated incident of this size would also lead to an inactivity leak, a form of emergency state for the network in which rewards and penalties are modified.
Mitigating the risk with diversification and a technical approach
Diversifying node operators is crucial to mitigating the risk of correlated slashing. By staking with multiple node operators across different geographic locations and infrastructure providers, stakers can help reduce the risk of simultaneous slashing. Diversification also helps in spreading one’s individual risk across multiple validators to reduce the impact of any single validator's failure.
A technical approach to diversification is essential to mitigate the risk of correlated slashing:
- Multi-client operations: Using different Ethereum clients (e.g., Prysm, Lighthouse, Nimbus) can protect against client-specific bugs.
- Geographic and cloud redundancy: Hosting validators in different geographic locations and on multiple cloud services ensures that local outages do not lead to mass slashings.
- Technical protections: Technical protections specific to Ethereum node operation are critical to mitigating the risk of a slashing incident taking place, including double-singing protection and failover.
- Diversifying node operators: Diversifying the active set across secure, independent node operators rather than staking via one centralized company’s infrastructure helps spread risk.
- Monitoring, alerting, and security: Implementing real-time monitoring and alerting systems, along with other security best practices, can help operators to quickly identify and rectify any issues that could lead to slashing.
Correlated slashing and liquid staking
Liquid staking participants receive a liquid staking token (LST) to evidence legal and beneficial ownership of the underlying staked token, along with any network rewards or penalties received. This LST represents a claim on the staked tokens and any rewards earned, comparable to a bailment in commodity law.
However, this also means that LSTs are exposed to the same slashing risks as the underlying staked tokens. If the validators associated with a liquid staking solution experience correlated slashing it can lead to a significant loss of redeemable ETH for the LST holders.
Participating in liquid staking protocols can help to mitigate the risk of correlated slashing when compared to staking with a single node operator. While many staking-as-a-service providers represent centralized node operators, some liquid staking protocols diversify their active set across operators.
It’s important to evaluate liquid staking offerings carefully as not all are designed to mitigate the risk of correlated slashing:
- Potential for shared operators: Some liquid staking solutions use one node operator for all of their staking. As more stake is onboarded to these sole node operators, the risk of correlated slashing also increases. This risk can be amplified for liquid staking solutions offered by one centralized entity, which may operate all staking on their own in-house infrastructure. A diversity of node operators within a liquid staking solution helps mitigate this risk for stakers.
- Lack of transparency and compliance: Participants may not be fully aware of the underlying validators or infrastructure in their liquid staking solution, making it difficult to assess the risk of correlated slashing. This is because many liquid staking protocols do not require that their node operators meet counterparty compliance requirements, and may generally lack transparency into their node operators. This can also make it difficult to assess a liquid staking solution’s validator performance and security standards overall, such as what technical protections the operator implements or what their client operations are.
Liquid Collective’s approach to mitigating the risk of correlated slashing
Liquid Collective aims to provide a decentralized approach to enterprise-grade liquid staking, addressing the need for the highest level of security and compliance while promoting diversity, standardization, and composability.
Liquid Collective has an intentional, targeted, and technical approach that aims to mitigate the risk of correlated slashing:
- Multi-operator approach: Liquid Collective’s active set is composed of independent, enterprise-grade Node Operators who abide by strict security standards, including Coinbase Cloud, Figment, and Staked. All ETH staked via Liquid Collective is delegated round-robin across the protocol’s diversified Node Operators, ensuring that no LsETH holder has all of their eggs in any one Operator’s basket. This operator diversity—while still ensuring operator compliance—is unique to Liquid Collective within the liquid staking market and is critical to mitigating the risk of correlated slashing.
- Technical protections: All Liquid Collective Node Operators are required to run enterprise-grade infrastructure to prevent against the risk of slashing, including implementing double-signing protection, operating nodes with multi-client and global distribution, and having robust failover methods in place.
- Security: All Liquid Collective Node Operators are also required to meet strict security standards, including maintaining cybersecurity programs, incident resolution, and meeting other enterprise-grade security standards.
- Compliance: Mandatory KYC/AML for all operators facilitates compliance and helps to mitigate against Node Operator counterparty risk for stakers.
- Transparency: Anyone can see rewards and Node Operator performance onchain.
- Slashing Coverage: To further mitigate against the risk of slashing, Liquid Collective offers built-in slashing coverage, including Nexus Mutual cover, to provide protection to all LsETH holders against both network-wide events and Operator failures.
What’s next
In addition to the protocol’s robust approach to mitigating the risk of slashing, Liquid Collective and Rated Labs announced a partnership to develop the Ethereum ecosystem's first open source validator performance and security standards to define industry-wide benchmarks for evaluating staking providers in July of 2023. This ecosystem-wide shared understanding of how to evaluate staking on a risk-adjusted basis is viewed as a crucial missing piece for the professionalization of the staking ecosystem overall.
Liquid Collective's task group will first align on the key parameters that will be used to objectively measure validator performance and security. The partnership also aims to build robust security management standards that effectively mitigate node operator risks, including:
- Correlated failures associated with concentrated deployments on cloud, regional, or client bases
- Liveness failures of beacon nodes and validator clients
- Key safety compromises at the validator client level
- Slashing safety compromise at the validator client level
Liquid Collective will leverage the completed methodology to natively embed programmatic parameters and service level agreements (SLAs) in the protocol's code, regarding validator attestations, missed rewards policies, validator security, validator onboarding management processes, and more, setting Liquid Collective apart as a pioneering protocol in offering such performance requirements and SLAs for stakers.
You stay tuned to the development of the standards by subscribing to monthly Liquid Collective Updates, or by following Liquid Collective on X.




